Image Encryption: Generating Visually Meaningful Encrypted Images
Introduction
To protect image contents, most existing encryption algorithms are designed to transform an original image into a texture-like or noise-like image which is, however, an obvious visual sign indicating the presence of an encrypted image and thus results in a significantly large number of attacks. To address this problem, this paper proposes a new image encryption concept to transform an original image into a visually meaningful encrypted one. As an example of the implementation of this concept, we introduce an image encryption system. Simulation results and security analysis demonstrate excellent encryption performance of the proposed concept and system.
New concept of image encryption
Most existing image encryption algorithms protect original images by transforming them into texture-like or noise-like encrypted images with a nearly uniform distribution of pixel values. As a result, the encrypted images can withstand different types of attacks, protecting original image information with a high level of security. However, this texture-like or noise-like feature is an obvious visual sign of encrypted images. It definitely catches more people’s attentions and thus brings a significantly large amount of attacks and cryptanalysis to encrypted images. The risk of information leakage, loss or modification exponentially increases.
On the contrary, a visually meaningful or good-looking image. This would significantly reduce the risk of an encrypted image being attacked and modified. This interesting phenomenon motivates us to propose a new concept for image encryption as shown in Figure 1. The idea of this concept is straightforward. It directly encrypts an original image into a visually meaningful encrypted image (VMEI). Because a VMEI has a visual feature similar to a normal image, attackers have extreme difficulty distinguishing VMEIs from large amount of normal images. Furthermore, for a given original image, as can be seen in Figure 1, various encryption algorithms or an encryption algorithm with different security keys may yield a large number of VMEIs with completely different appearances or formats. This further increases attackers’ difficulty of obtaining the correct VMEIs before their cryptanalysis. Thus, the proposed concept is able to protect original images with a much higher security level than most existing encryption algorithms.
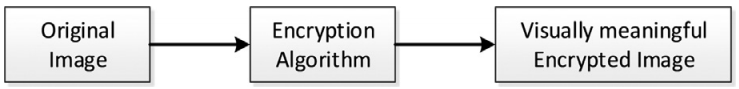 |
| Figure 1. The new concept of image encryption. |
New image encryption system
The key issue of the proposed concept is how to generate VMEIs. Motivated by technologies of image hiding and watermarking, this section introduces a new image encryption system (NIES) as an implementation example of the proposed concept.
Figure 2 shows the structure of NIES. The underlying fundamental idea of NIES is that it uses a normal image as the reference image and yields a VMEI that has an appearance similar to the reference image. NIES consists of two parts: a pre-encryption process and a discrete-wavelet-transform-based content transform (DWTCT). The pre-encryption process uses permutation and substitution to change image pixel locations and values. The pre-encrypted image is usually a noise-like image. It is then transformed by DWTCT into a VMEI that is visually similar to the reference image. Figure 3 shows an illustrate example of NIES.
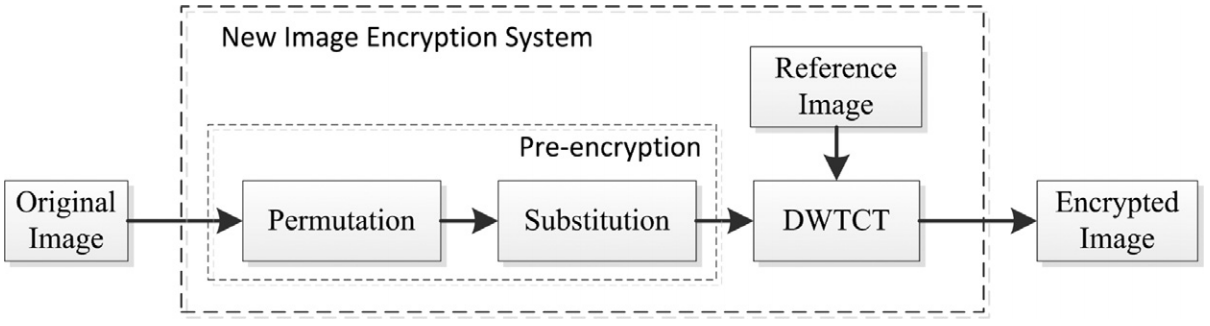 |
| Figure 2. The block diagram of the new image encryption system. |
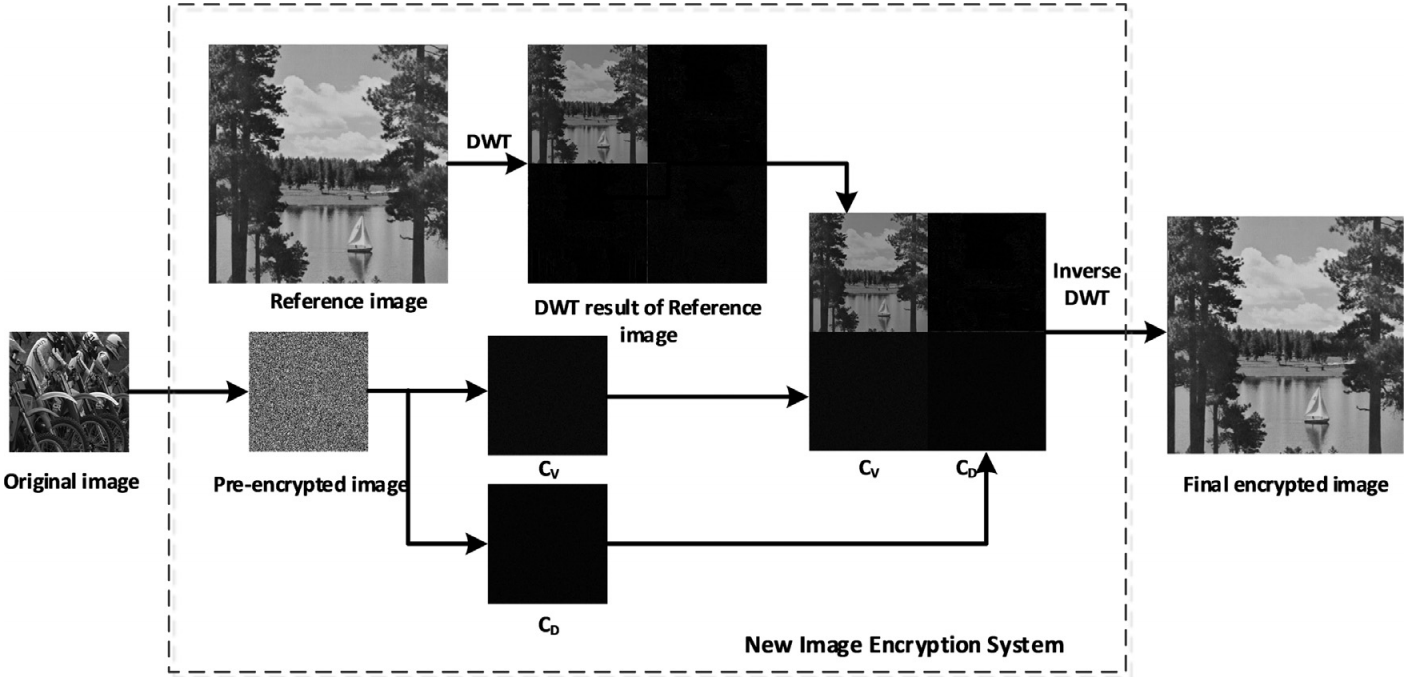 |
| Figure 3. An illustrative example of NIES |
Different from existing methods
Even though NIES is motivated by technologies of image hiding and reversible watermarking DWTCT differs from these in the following aspects:
(1) Different objectives. The objective of image hiding and reversible watermarking is to embed secret messages or watermarks into a cover image while minimizing distortions to the cover image. The resulting stego image (image with embedded messages/watermarks) is extremely similar to the cover image. Thus, the unauthorized users have difficulty of detecting the existence of messages or watermarks using various computer tools. On the other hand, the objective of DWTCT is to solve the security weakness of noise-like encrypted images generated by existing image encryption algorithms. It transforms the noise-like or texture-like appearance of the pre-encrypted image into a visually meaningful one and provides an additionally visual protection to the images on top of security provided by existing image encryption algorithms. Moreover, reversible watermarking intends to reconstruct both watermarks and the cover image without any distortion, while DWTCT recovers only the pre-encrypted image but not the reference image.
(2) Different requirements. In NIES, as long as the final encrypted image is visually meaningful for the person, its similarity to the reference image is not important to DWTCT. That is, NIES considers only naturalness of visual quality of the final encrypted image, while image hiding and reversible watermarking prefer the high similarity between the stego image and cover image. This naturalness property ensures that the final encrypted image has a high possibility to be regarded as a normal image. For real-time applications, DWTCT is required to be time efficient and a low computation cost. On the contrary, image hiding or reversible watermarking embeds messages or watermarks while minimizing distortions to the cover image, without considering the computational cost.